TLDR:
- Firebase allows for easy misconfiguration of security rules with zero warnings
- This has resulted in hundreds of sites exposing a total of ~125 Million user records, including plaintext passwords & sensitive billing information
After the initial buzz of pwning Chattr.ai had settled down, we set to work on scanning the entire internet for exposed PII via misconfigured Firebase instances.
Attempt 1
MrBruh wrote up a rudimentary scanner in Python that would check for Firebase configuration variables in websites or their loaded .js bundles.
It worked... until it didn't.
Turns out that a Python program with ~500 threads will start to chew up memory over time. For us that meant it was OOM'ing within an hour of starting it.
Attempt 2
Logykk rewrote the scanner in Go, unlike the prior it didn't seem to leak memory.
Our initial estimate was that this was going to take ~11 days to scan through the 5 1/2 Million domains, but it turned out to be closer to 2-3 weeks which made this very much a waiting game.
Manually checking every domain
We first went and started manually looking at each entry in the 550k line text file, seeing if we could find anything interesting, this was time consuming and very repetitive.
In the end, we went through quite a lot of it and had 136 sites and 6.2 million records, but we all knew that we needed to do something fully automated, because this was taking way too long.
Catalyst
Once we had acquired our shortlist of potentially affected sites we ran it through a secondary scanner that Eva had made called Catalyst.
This would take the site (or .js bundle) we found, then automatically check for read access to common Firebase collections & any that were explicitly mentioned in the JavaScript itself.
When it found read access to a collection it would attempt to calculate the impact of the exposed data by gathering a sample of 100 records, checking the type of information contained and extrapolating that by the total size of the collection.
We then, decided the database to use to store all of these results, and we chose Supabase (which uses PostgreSQL under the hood) a open source Firebase competitor, just for the irony.
Once all that had been completed the data was formatted and uploaded to a private database table.
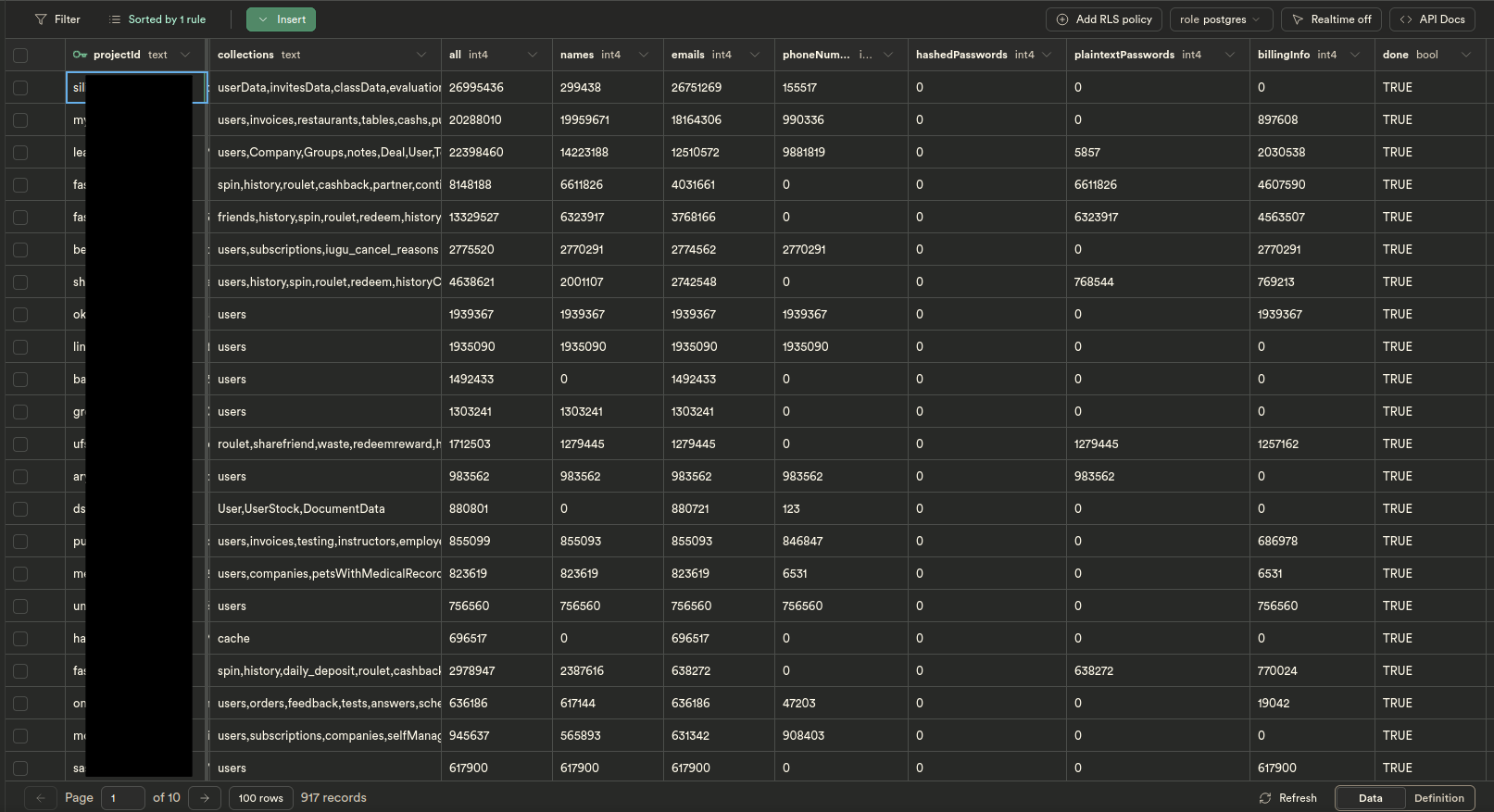
The Numbers
- All (records): 124,605,664
- Names: 84,221,169
- Emails: 106,266,766
- Phone Numbers: 33,559,863
- Passwords: 20,185,831
- Billing Info (Bank details, invoices, etc): 27,487,924
These numbers should be taken with a grain of salt. They are likely larger than shown here.
The Shortlist (of affected sites)
1. Silid LMS
- Learning management system for students & teachers
- Most total exposed user records, at 27 Million affected users. (Names, Emails & Phone numbers)
2. Online gambling network

- Comprised of 9 sites which are all reskins of each other.
- Some spins are rigged to have a 0% chance of winning.
- Customer support tried to flirt with me when attempting to report the issue.
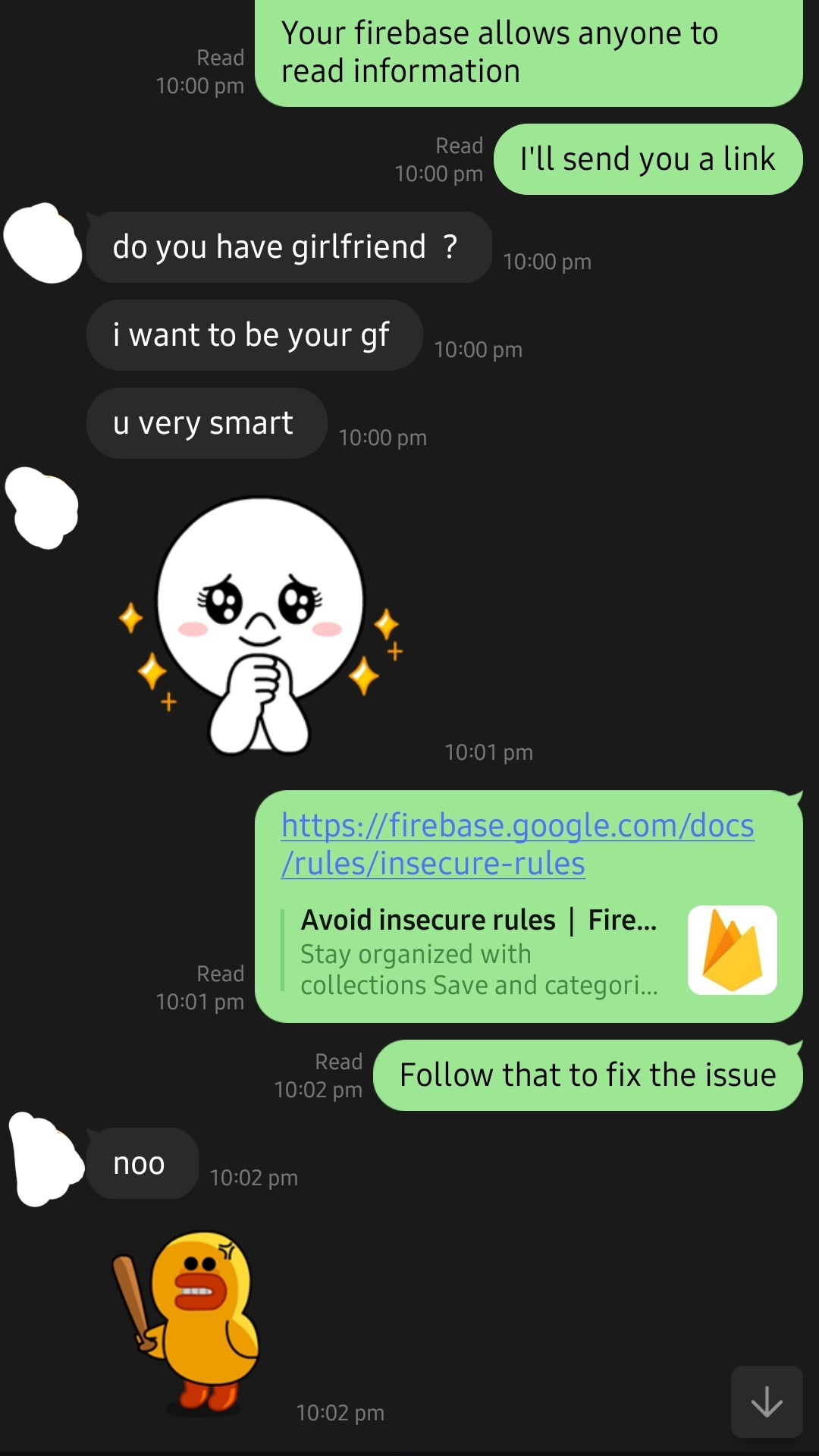
- Contains the most amount of exposed bank account details (logins) out of all of our records. (8 Million)
- Also contains the most plaintext passwords out of all of the affected websites, at 10 Million passwords being exposed.
3. Lead Carrot
- Online “lead” generator for cold calling
- Top 3 in total amount of exposed user information, sitting at 22 Million affected people.
4. MyChefTool
- Business management app & Point of Service application for restaurants
- 1st place for most exposed Names & 2nd place for exposed Emails. (14 Million & 13 Million respectively)
The aftermath
- 842 Emails sent over 13 days
- 85% Emails delivered
- 9% Emails bounced
- 24% of Site owners fixed the misconfiguration
- 1% of Site owners emailed us back
- 0.2% (2) Sites owners offered a bug bounty